What is AES?
An overview of Advanced Encryption Standard
Please, tell me more about this magic that you call cryptography!
AES stands for Advanced Encryption Standard. Each block of this cipher takes in a 128bit message and a 128bit key. This cipher is used by the US Government to protect classified enformation, and is used to encrypt sensitive data all around the world! The algorithm was developed by two cryptographers: Joan Daemen and Vincent Rijmen from Belgium, as a replacement for DES, Data Encryption Standard, which was the widely used standard for encryption before AES was developed.
So let's go over how AES works!!
We will use an example of our secret message and secret key shown below. Both converted to ASCII hexcode.
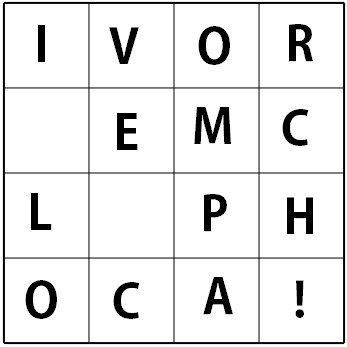
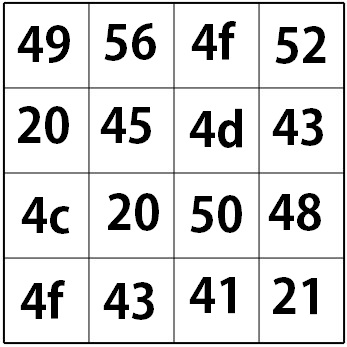
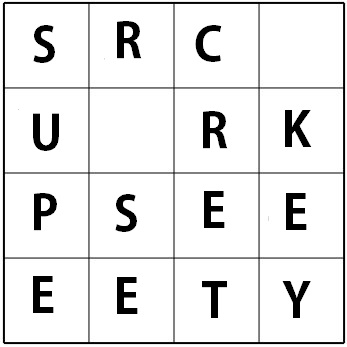

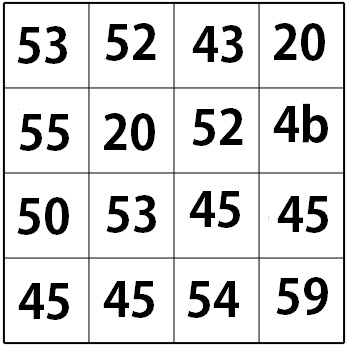
Key Expansion
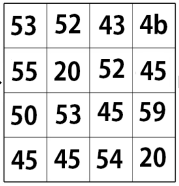
First, the key needs to be expanded to create the keys to be used in later rounds of the encryption. This is done in the process of key expand. At the highest level, key expand takes in one key, and outputs 10 new keys. The first step of the key expand is to shift the bytes of the last column. The top byte goes to the bottom, and the rest shift up.

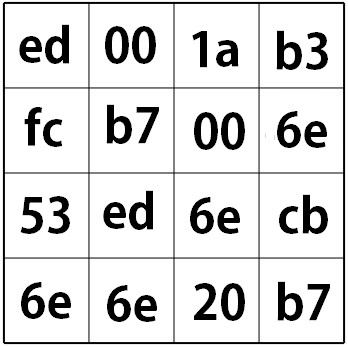
 Next, this key is passed through the s-box, which we will cover in more detail later!
Basically, the s-box maps each byte of the key to a new byte. This can actually be done with some matrix math, but conceptually can be simplified to a big look up table.
Here is the value of our key after passing it through the s-box:
Next, this key is passed through the s-box, which we will cover in more detail later!
Basically, the s-box maps each byte of the key to a new byte. This can actually be done with some matrix math, but conceptually can be simplified to a big look up table.
Here is the value of our key after passing it through the s-box:
 The next step is to XOR the last column of this matrix with the Round Constant. This is different constant for each of the 10 rounds, but is [01 00 00 00]^T for round1.
The next step is to XOR the last column of this matrix with the Round Constant. This is different constant for each of the 10 rounds, but is [01 00 00 00]^T for round1.
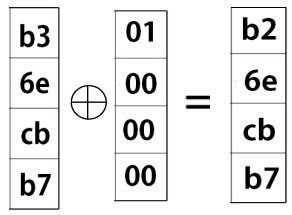 Then XOR this resulting column, with each column of the output key from the sbox, to get our new key for Round 1.
Then XOR this resulting column, with each column of the output key from the sbox, to get our new key for Round 1.

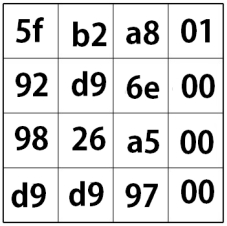 = Round 1 Key
Repeat these steps using the Round 1 key as an input to get the subsequent keys for rounds 2-10!
= Round 1 Key
Repeat these steps using the Round 1 key as an input to get the subsequent keys for rounds 2-10!
Initial Round
Once the keys are all set, we can get started with the other encryption steps. First is the initial round. The initial round is actually quite simple! All you need to do is xor each bit of the message with each bit of the initial key.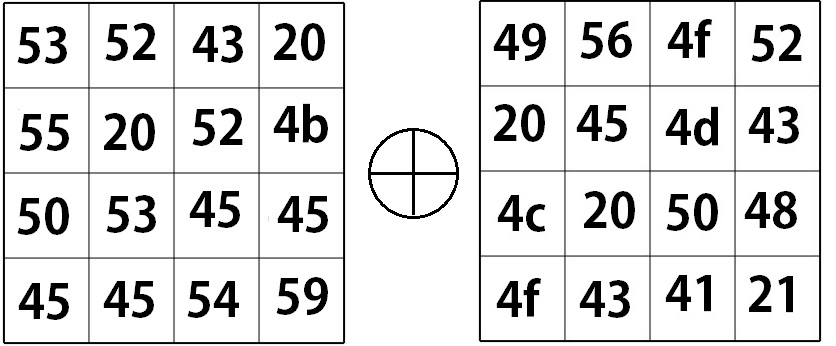

 = Round 0 Output
= Round 0 Output
Other Rounds
Rounds 1-10 of the cipher are a bit more complicated. Each round contains 4 major steps.- Substitute bytes
- Shift Rows
- Mix Coluns
- Add Round Key
Substitute Bytes
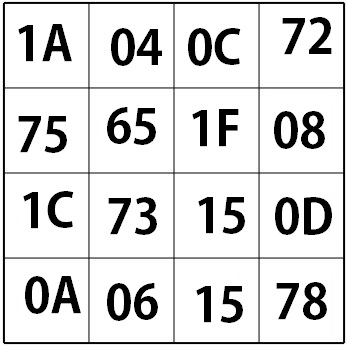
This is the same s-box byte-mapping as we used earlier in the key-expand! It applies two math functions to the matrix. First it takes the inverse, and second it multiplies by a constant matrix using Gallois Field matrix multipliation , and then adds a 8bit constant column. This can be simplified to a look up table to perfom the s-box transformation. The s-box result for our example is shown below.

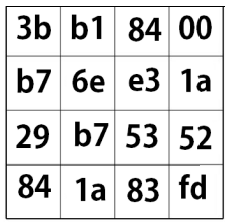
Shift Rows
In this step, you shift the rows to the left and wrap them around to the other side. How many bytes of the row shifts increases as the rows descend from top to bottom. Our example shows how this occurs.

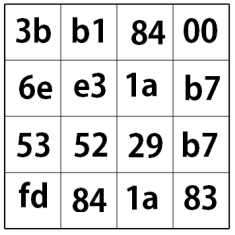
Mix Columns
Similarly to the S-Box transfomation, Mix Columns treats each column as a poolynomial, and is essentially a matrix multiplication. This re-orders the bits of each columnn in a very specific way.

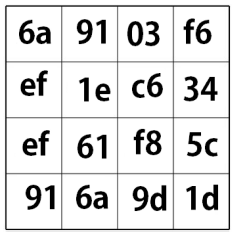
Add Round Key
This step is just like the operation we did in the initial round! Remember the Round1 key we found in key expansion earlier? We XOR that key with the result of mix columns to get the output of Round 1!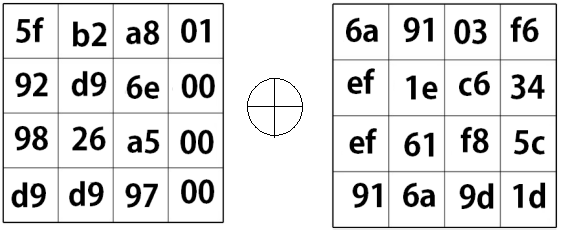

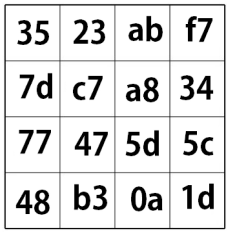 = Round 1 Out
= Round 1 Out
Repeat!
Now repeat all these steps for rounds 2-9! Round 10 is nearly identical except you skip the mix-columns step. After all this your final cipher should be the string shown below.
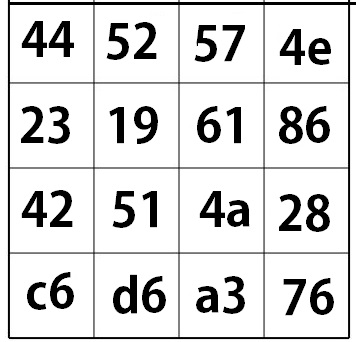
D # B Æ R . Q Ö W a J £ N . ( v
Decryption!
Now you know how AES Encryption works!! To decrypt your message from the resulting cipher text, use the same key-expand, and simply perform each step in reverse!
The End
Good luck, and happy encrypting! :)